GitHub - guess-js/guess: 🔮 Libraries & tools for enabling Machine Learning driven user-experiences on the web
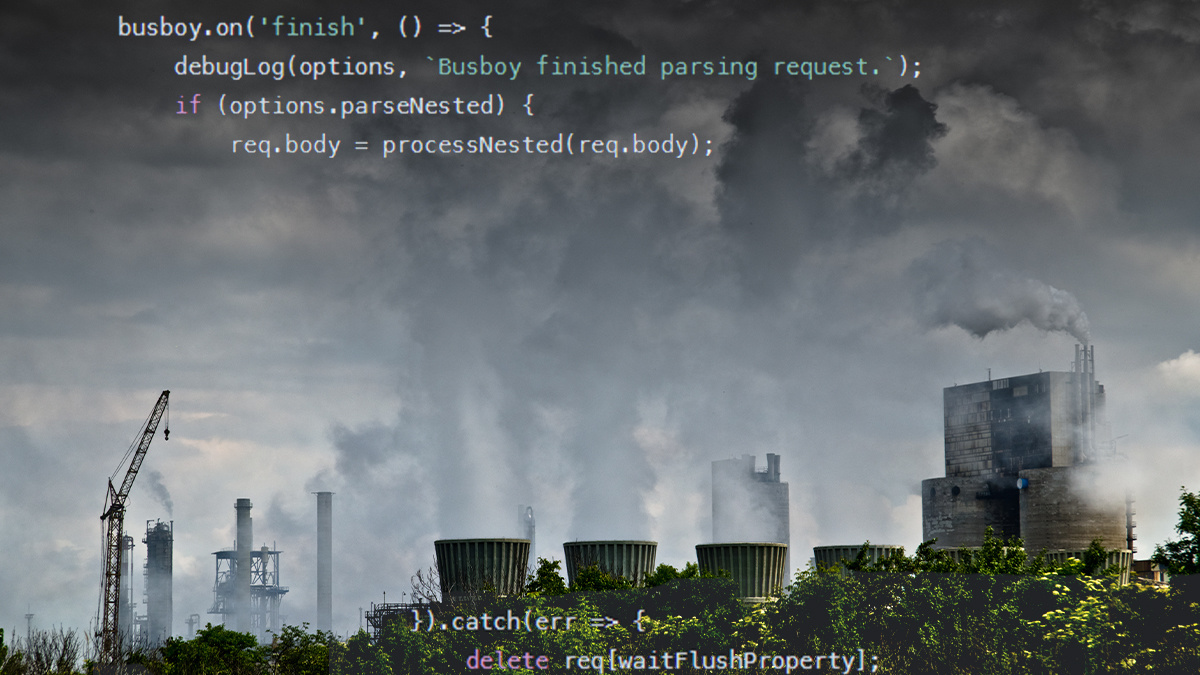
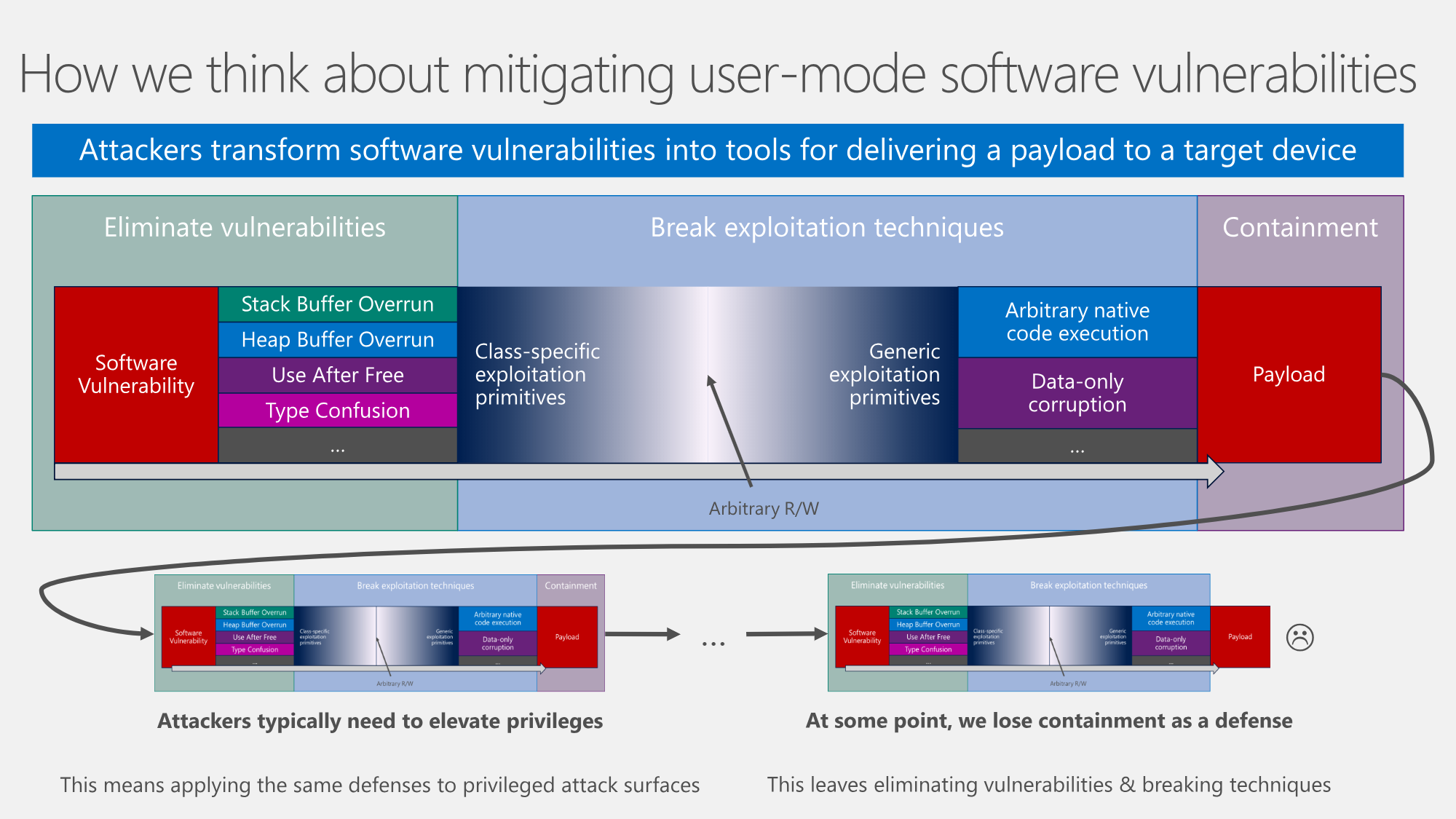
Prototype pollution: The dangerous and underrated vulnerability impacting JavaScript applications | The Daily Swig

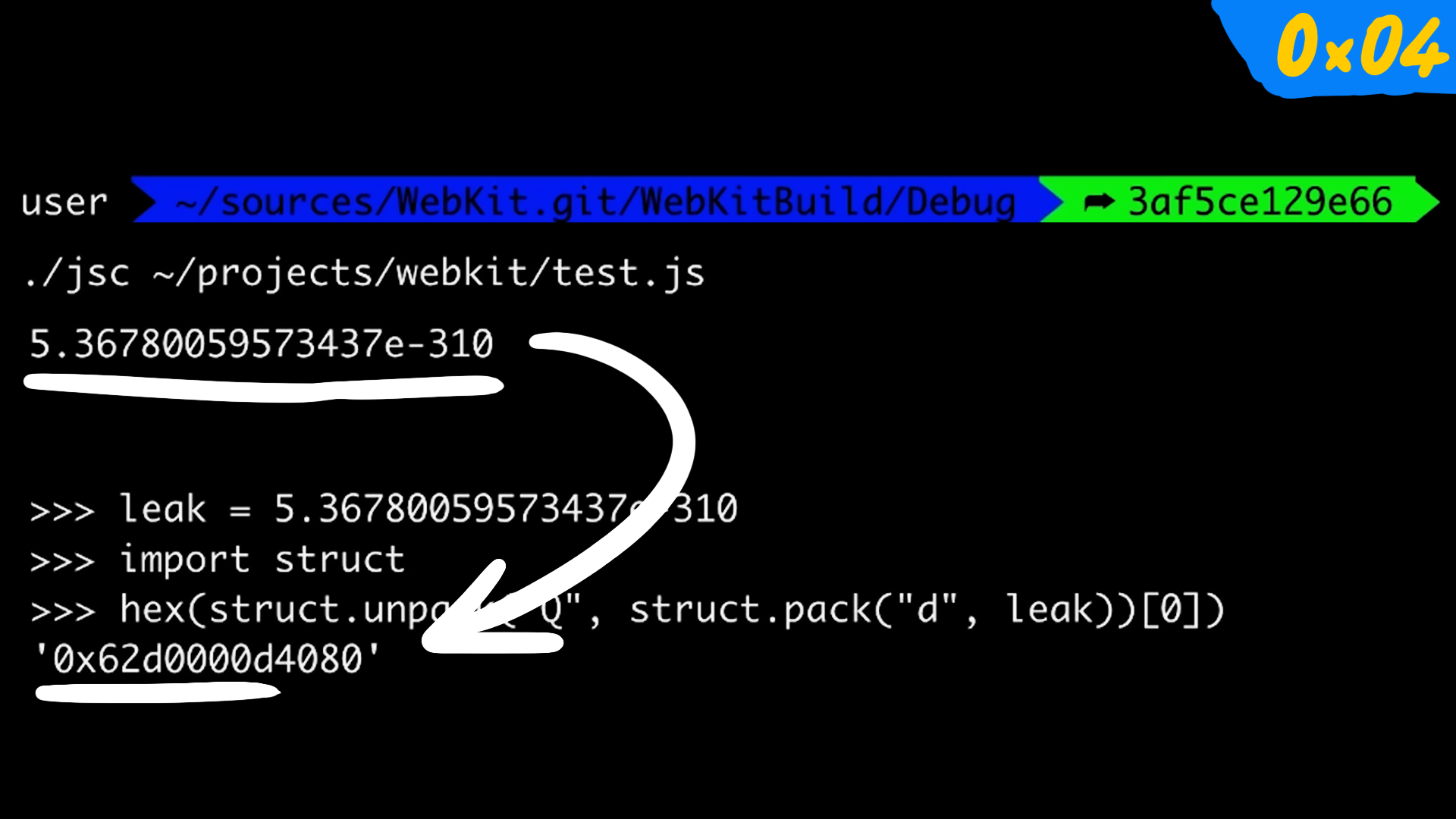
alexrad on Twitter: "Ubiquiti patched CVE-2023-23912 from pwn2own. It is a very simple shell command injection vulnerability, reachable from one hop upstream, affecting EdgeRouters and UniFi Security Gateways. The network domain is

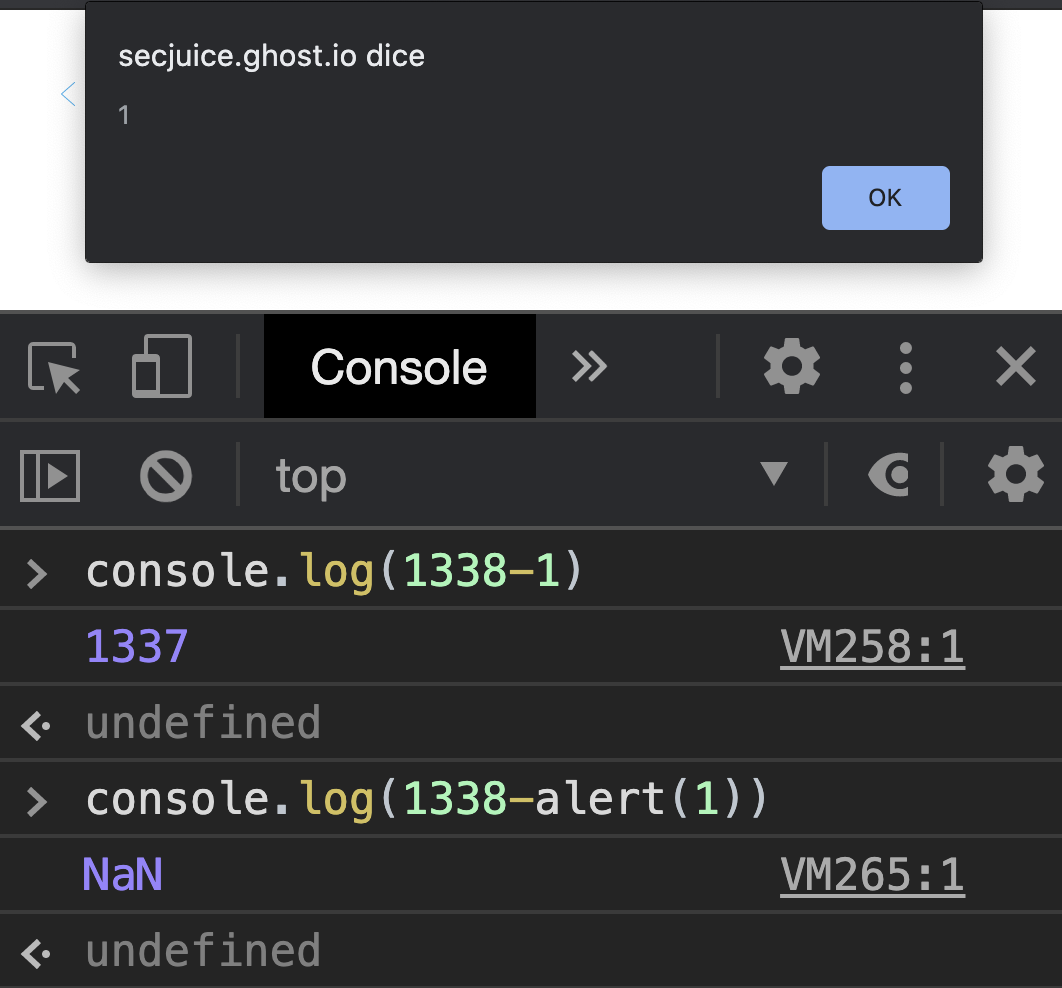
Remote code execution vulnerability exposed in popular JavaScript serialization package | The Daily Swig
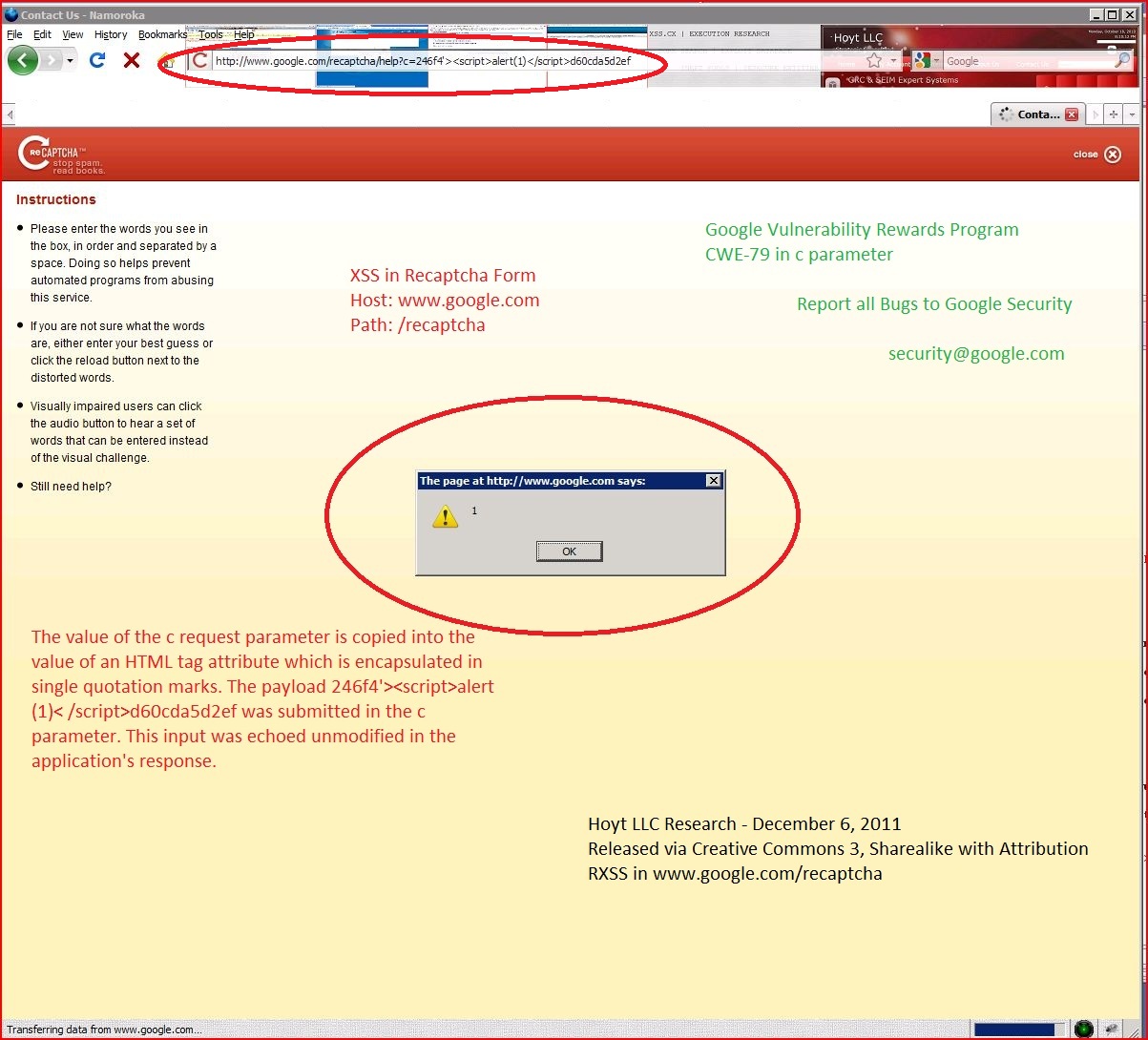
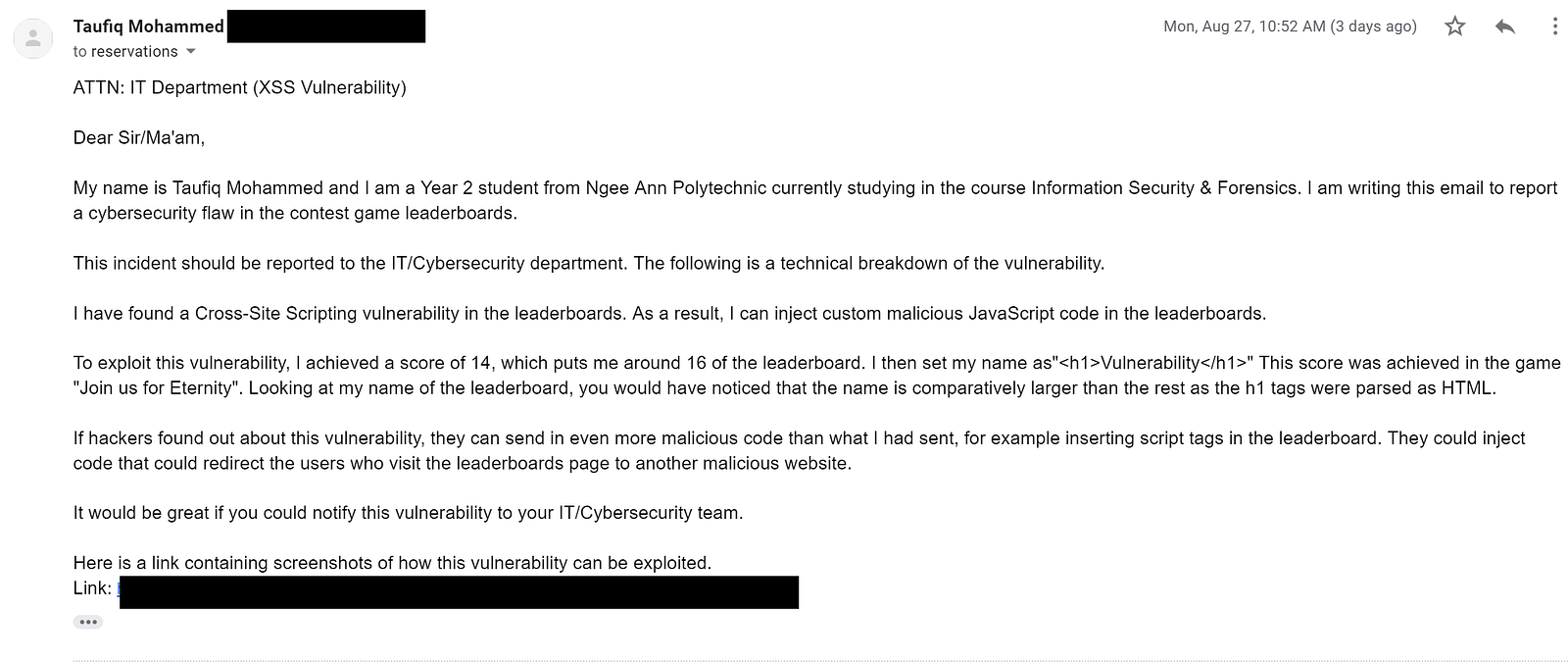
Google Vulnerability Rewards Program, XSS, Best Practices, Vulnerability Management, Captcha Form, google.com
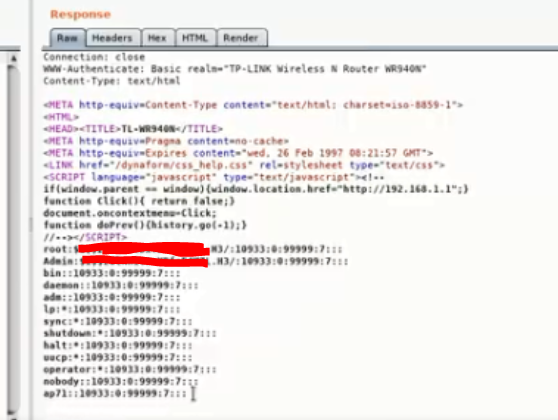
Directory Traversal Vulnerability In TP-Link Wireless N Router WR940N | by Farhan Khursheed | Medium