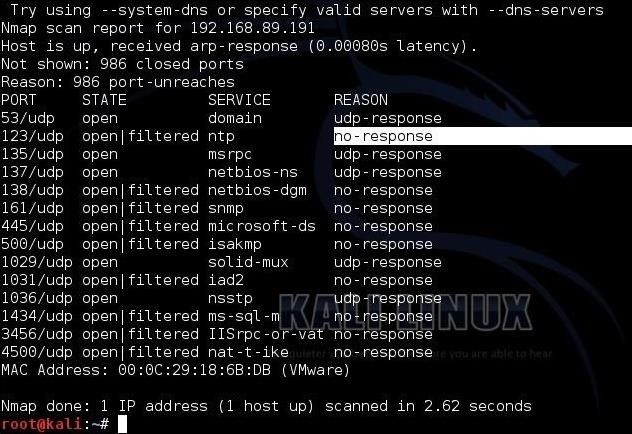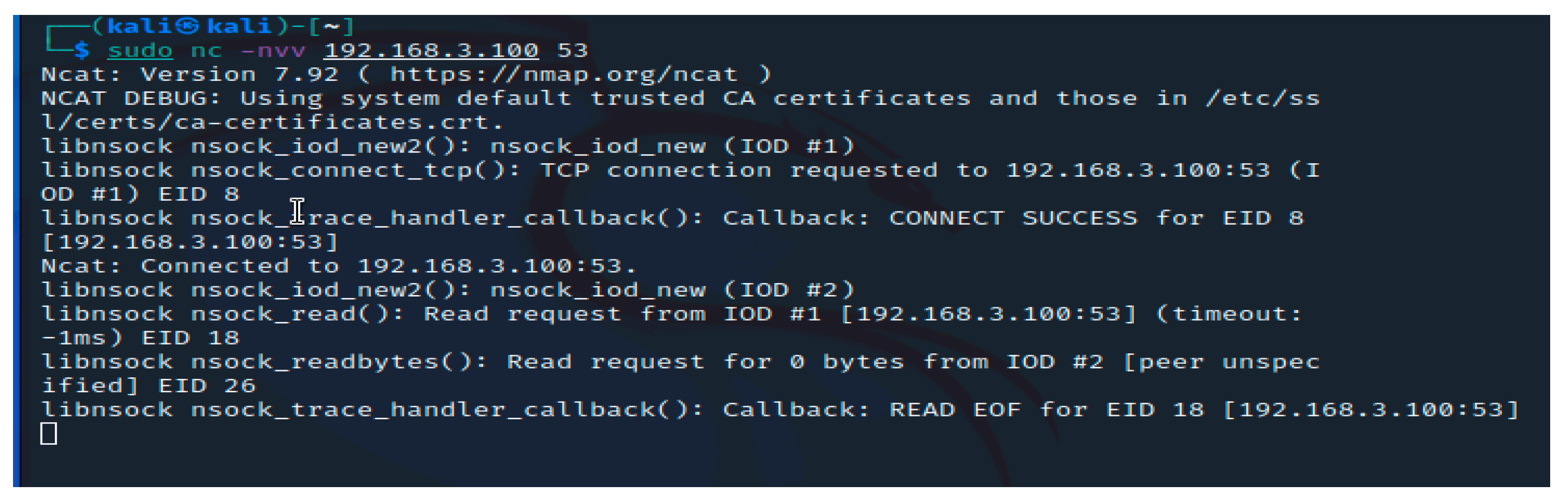
Sensors | Free Full-Text | Research on Security Weakness Using Penetration Testing in a Distributed Firewall

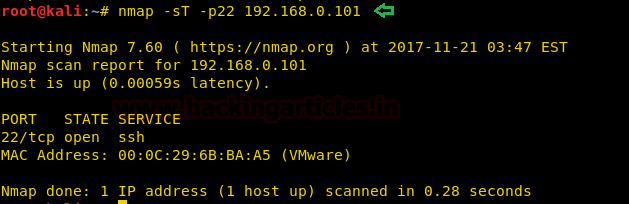
Evading Firewall/IDS during network reconnaissance using nmap | by Prateek Parashar | InfoSec Write-ups
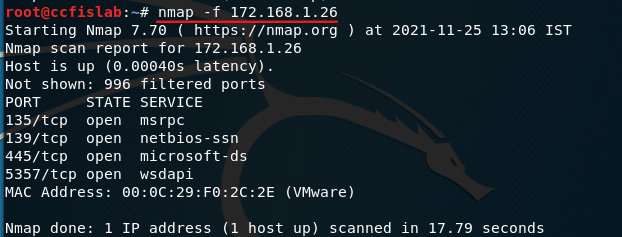
Evading Firewall/IDS during network reconnaissance using nmap | by Prateek Parashar | InfoSec Write-ups
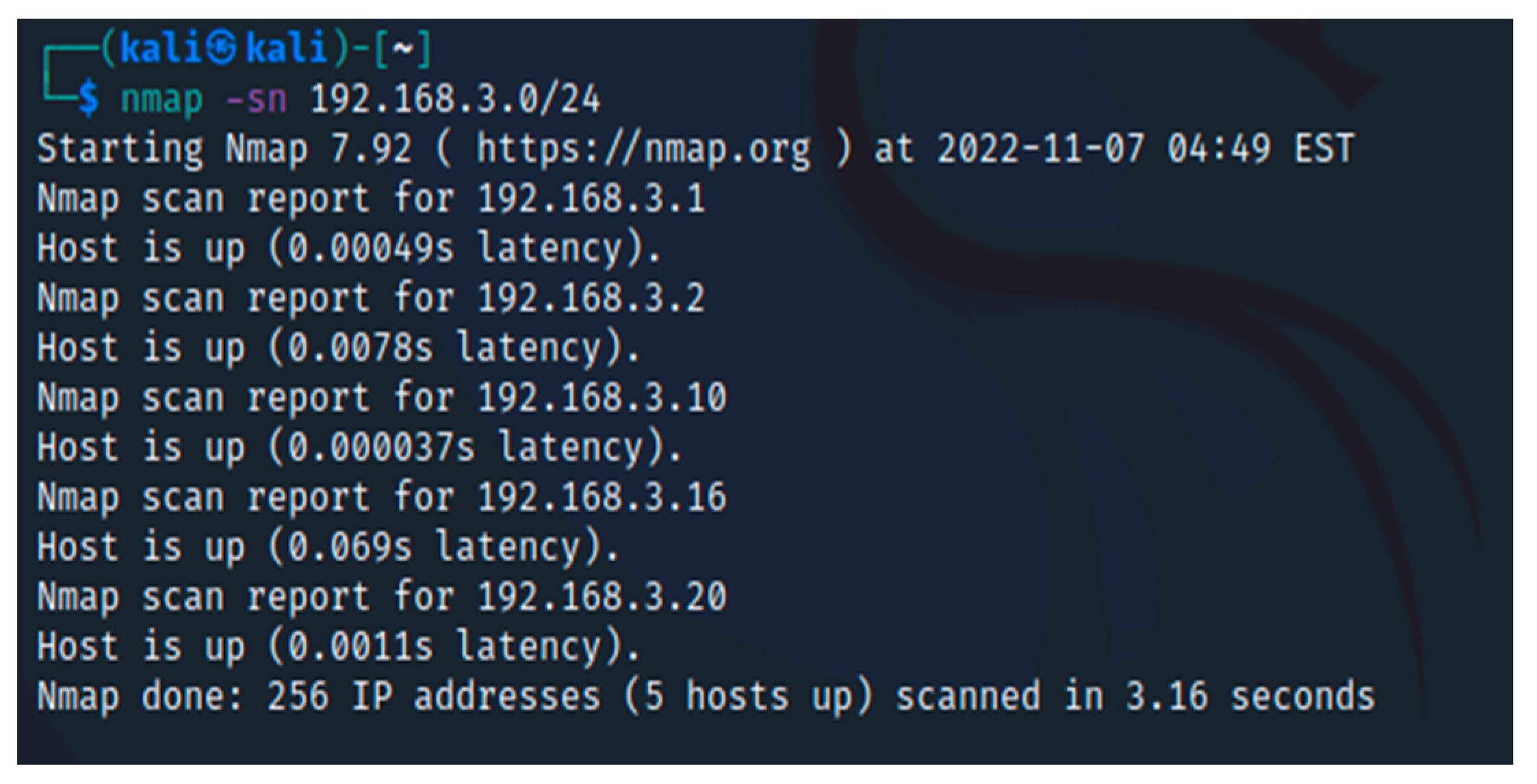



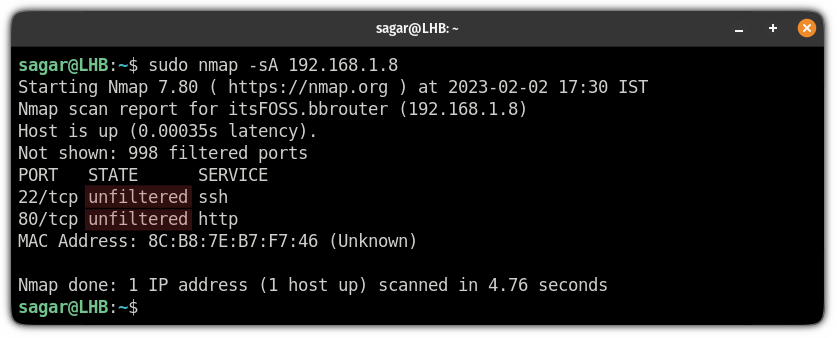


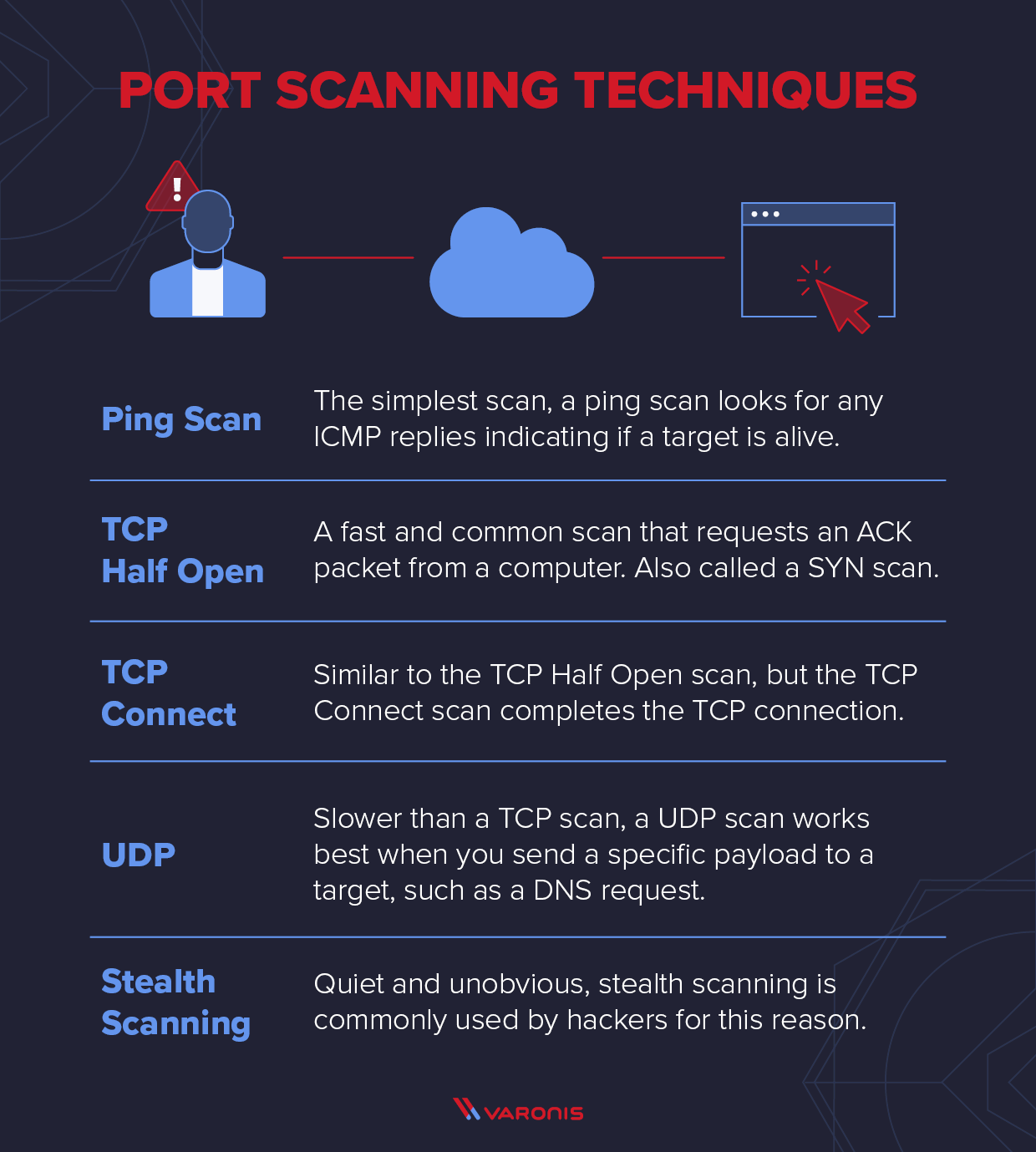

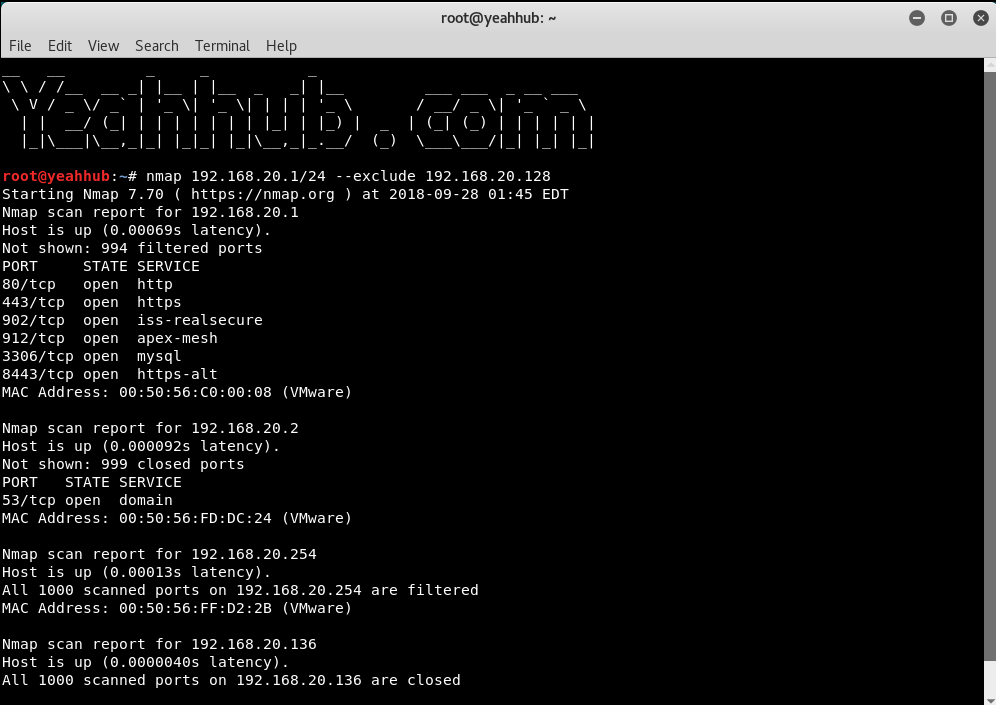
![Nmap evade firewall and scripting [updated 2019] | Infosec Resources Nmap evade firewall and scripting [updated 2019] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/082912_1952_NmapEvadeFi4.jpg)
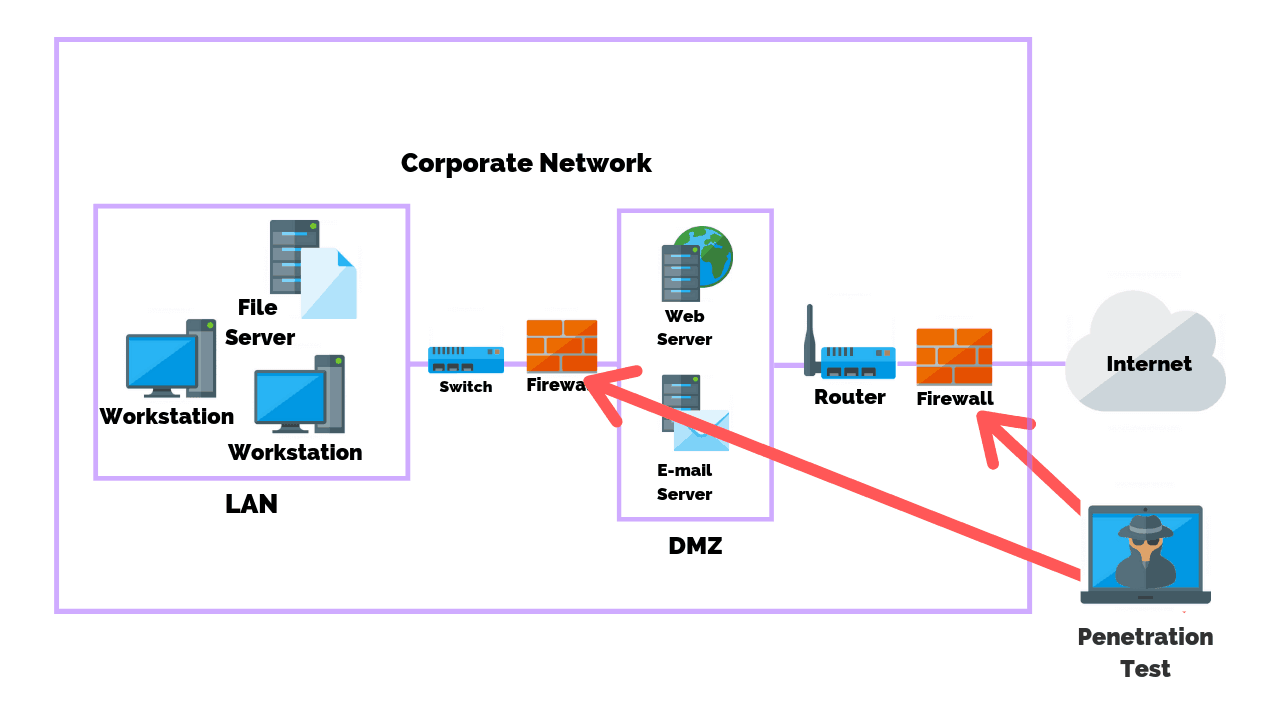
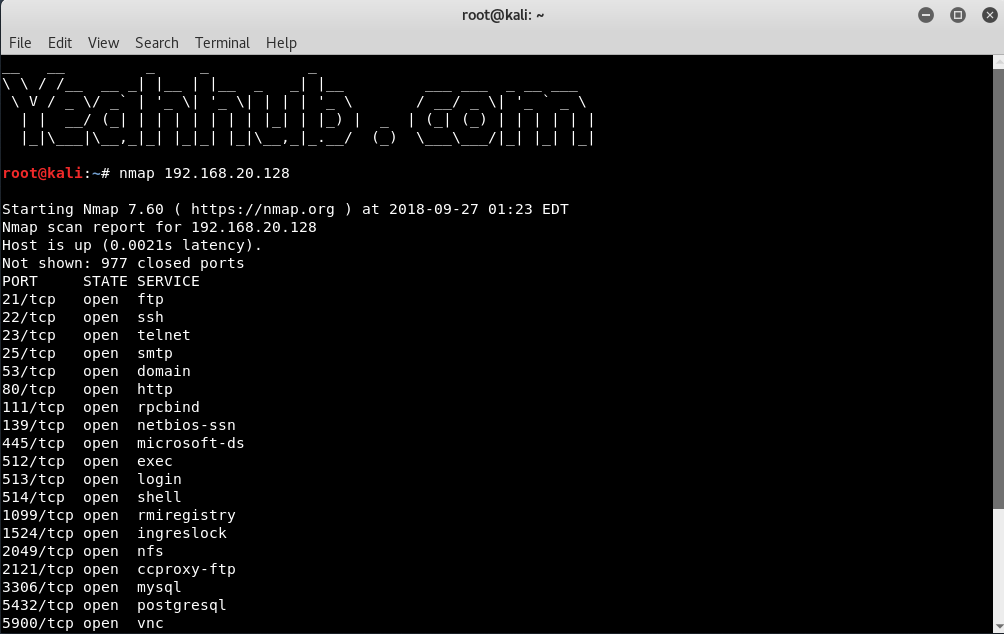
![Nmap evade firewall and scripting [updated 2019] | Infosec Resources Nmap evade firewall and scripting [updated 2019] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/082912_1952_NmapEvadeFi1.jpg)